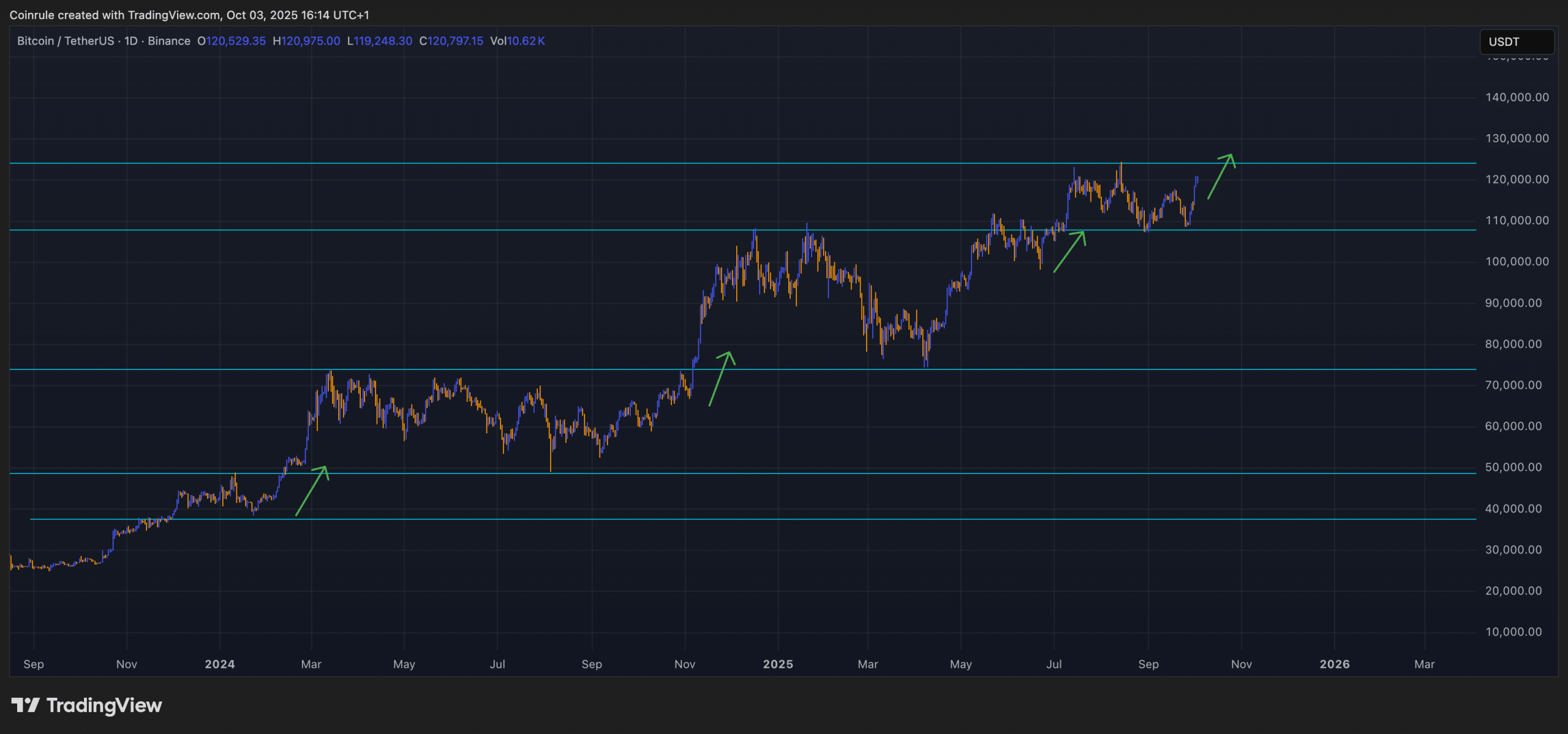
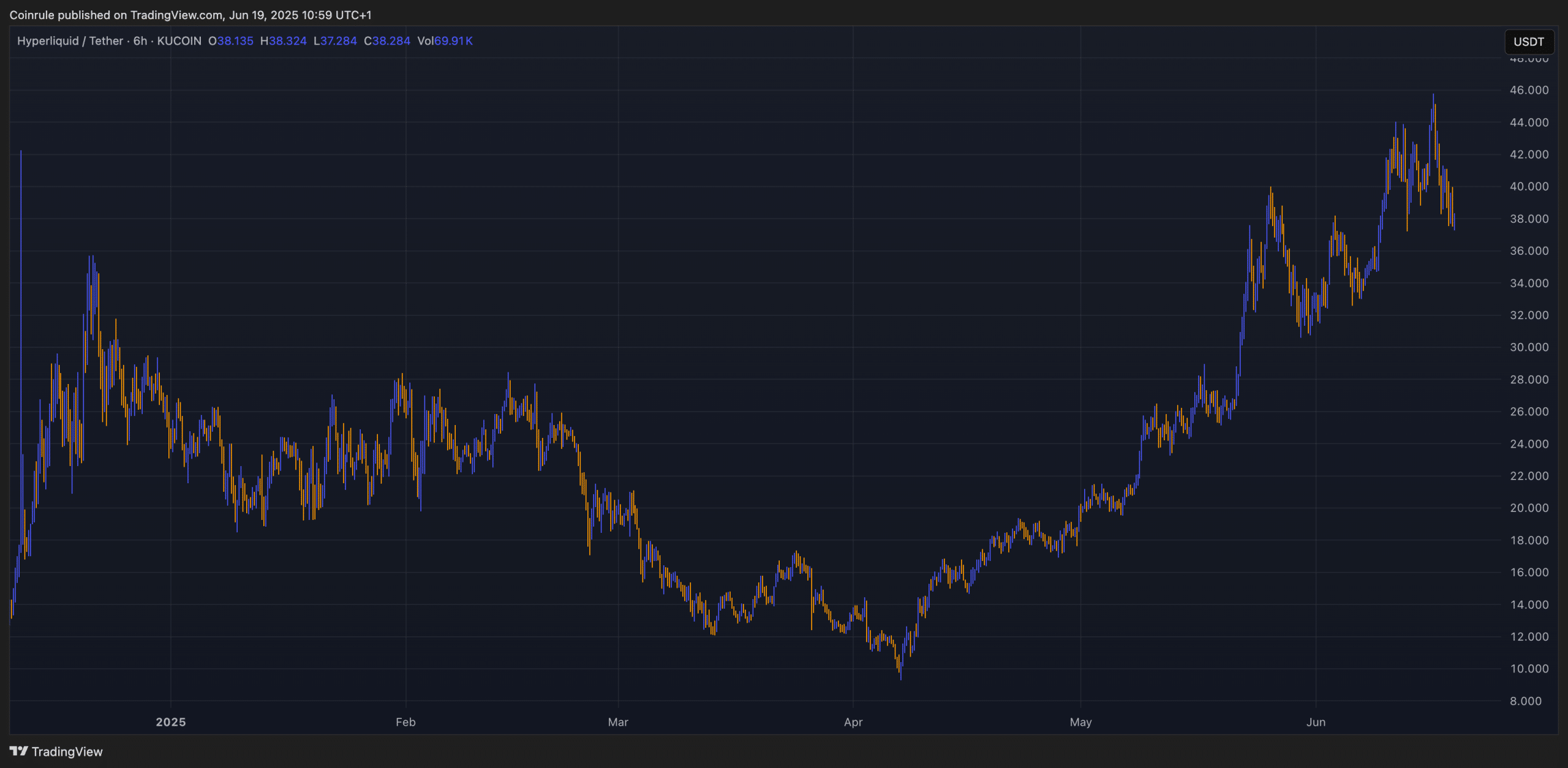
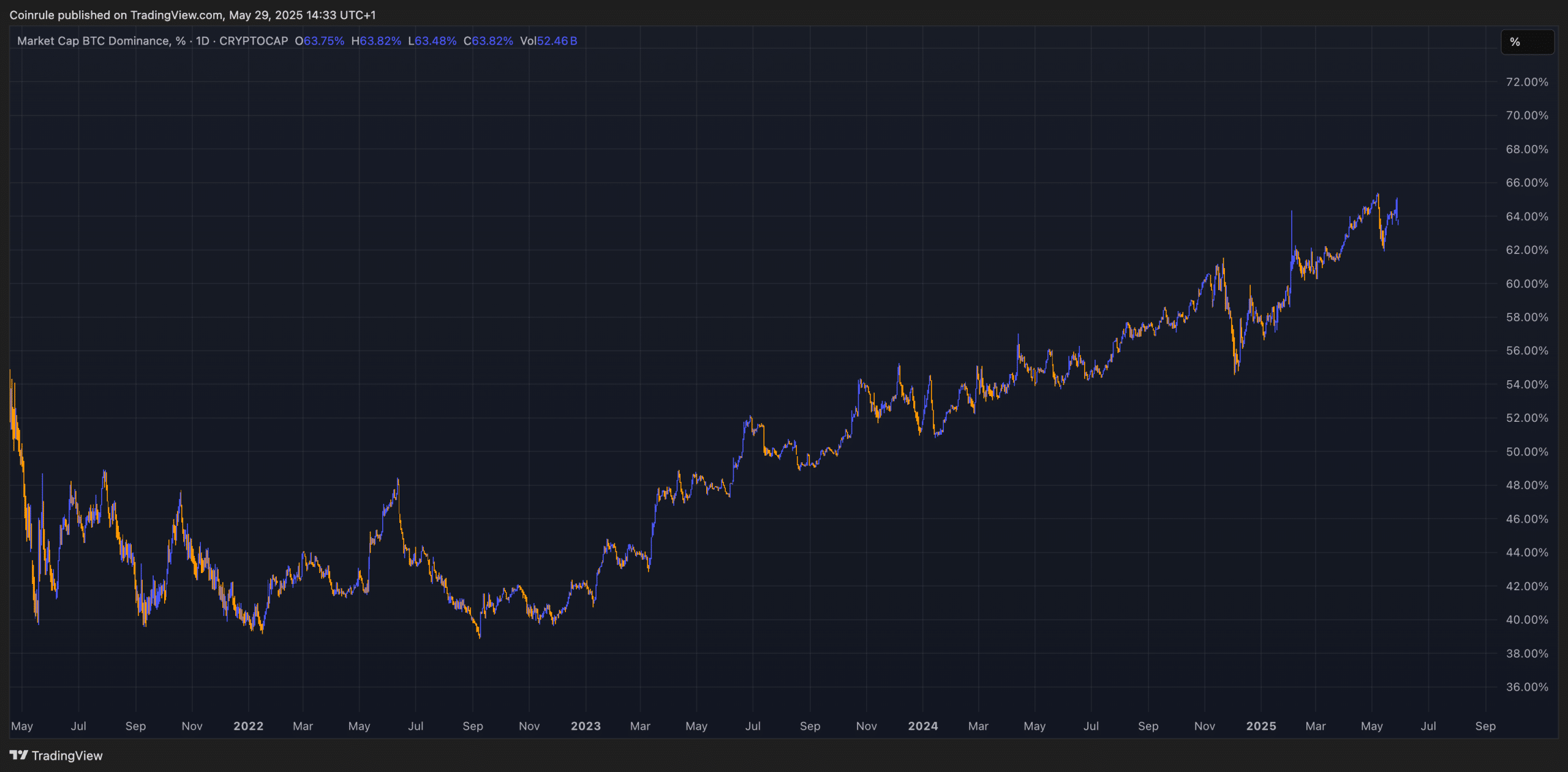
Coinbase Financial Markets Now Live on Coinrule with Perpetuals Trading
Perpetual futures have arrived for Coinbase US Traders on Coinrule! Launch lightning-fast strategies with indicators, time entry points, or DCA into positions with just a few clicks. Backed by Y Combinator, trusted by 350k+ traders, and with 1M+ strategies live, Coinrule puts elite trading at your fingertips. For the first time, you can now connect Coinrule to Coinbase Financial Markets and start building automated trading strategies for derivatives! What Does This Mean for Coinrule’s American…